Application in Wireless Encryption Technology of Mifare Card Access Control
With the advancement of technology, the access control system has gradually evolved from the original door guard and key to open the door to the current non-contact card access control system, that is, the Mifare card access control system. The non-contact smart card access control management system has outstanding advantages such as advanced technology, stability and reliability, and better performance-price ratio than other access control products, and can be widely used in various industries. In today's increasingly widespread application of Mifare cards, Mifare card access control systems have gradually replaced other existing access control and become the mainstream method of access control systems with the safe, reliable, efficient, flexible and convenient access control management.

Working Principle of Mifare Card Access Control System
In the application of induction technology, card reader continuously emits a 125kHz electromagnetic field through its internal coil, this magnetic field is called the "Excitation Signal". When an induction card is placed within the reading range of the card reader, the coil in the card generates a weak current under the induction of the "Excitation Signal", which serves as the power supply for a small integrated circuit in the card, and the integrated circuit in the card stored with the unique digital identification number (ID) entered during manufacture, this number is transmitted from the card back to the card reader through a 62.5kHz modulated signal, which is called the "Received Signal". The card reader transmits the received wireless signal back to the controller, which is processed, error-detected and converted into a digital signal, the controller then sends this digital ID number (ID) to the microprocessor on the controller, it makes the traffic decision.
Encryption of Mifare Card Access Control
1. DES Algorithm Encryption Technology
The DES algorithm encryption technology adopts a symmetric cryptographic system, most of the symmetric algorithms have the same encryption/decryption keys, the program design is simple and reliable, the resource cost is less than that of the convention cipher, and the operation speed is high. The disadvantage is the heavy workload of key distribution, exchange and management. The pseudo-random sequence generator in the management server generates a 56-bit key. Weak and semi-weak keys are automatically eliminated. All cards and card readers in the entire system are compiled with product serial numbers, and the management server automatically assigns a corresponding different key to each product serial number, making a key table for use, and completing key distribution.
2. National Secret Encryption Algorithm
The non-contact chip card which supports the National Cryptographic Bureau's cryptographic algorithm is popular all over the world, and the popularity of the adoption by all walks of life is unexpected by the chip manufacturer. Although chip manufacturers have introduced related upgrade chips, these chips have not been accepted by most markets due to factors such as price and technology popularization. In order to ensure the healthy and orderly development of my country's smart card market, with the support and organization of the State Cryptography Administration, the cryptographic algorithm has also been highly praised and followed by many integrated circuit chip manufacturers in my country, and related products have been successfully launched.
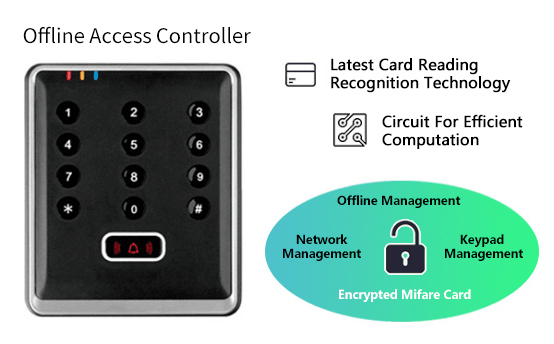
The working mode, system size, security, reliability, system cost and other factors of Mifare card access control system are often contradictory. It is unrealistic to use a so-called standard system model to meet all the requirements in practice, only by weighing the pros and cons and choosing the scheme according to the specific situation can we design a practical system.
Recommended reading 《Discussion on Smart Lock Becomes the "Dark Horse" of Access Control System》